Who would have imagined back in 1973 when Martin Cooper/Motorola dialed the first portable cellular phone call, that one day we'd be booking airline tickets, paying bills, taking pictures, watching movies, getting directions, emailing and getting work done on a little device the size of a deck of cards. As these 'cell-phones' have matured, they've also become an integral part of our lives on a daily basis. No longer are they strictly for emergency situations when you need to get help, now they are attached to our hip with an accompanying ear apparatus as if we've evolved with new bodily appendages. People have grown accustomed to being 'connected' everywhere. There have been mobile breakthroughs over the years, like having 3G/4G networks and Wi-Fi capability, but arguably one of the most talked about and coveted mobile devices in recent memory is the Apple iPhone.
Ever since the launch of the iPhone in 2007, it has changed the way people perceive and use mobile devices. It's not just the tech-savvy that love the iPhone, it's Moms, Florists, Celebrities, Retailers and everyone in between that marvel at the useful ways iPhone can be used, and for their very own novel purpose. There are literally hundreds of thousands of apps available for iPhone, from the silly and mundane to banking and business. Browsing the web is a breeze with the iPhone with the ability to view apps in both portrait and landscape modes. The ability to zoom and 'pinch' with just your fingers made mobile browsing tolerable, even fun from an iPhone. Shopping from your cell phone is now as common as ordering a cup of coffee - often at the same time! iPhone developers are pushing the limits with augmented reality applications where you can point your iPhone into the sky and see the flight number, speed, destination and other such details as planes fly by.
When the iPhone was first introduced and Apple started promoting it as a business capable device, it was missing a few important features. Many enterprises, and small businesses for that matter, use Microsoft products for their corporate software - Exchange for email, Word for documents, Excel for spreadsheets and PowerPoint for presentations. Those were, as expected, not available on the iPhone. As new generations of iPhones hit the market and iOS matured, things like iPhone Exchange ActiveSync became available and users could now configure their email to work with Exchange Server. Other office apps like Documents-to-Go make it possible for iPhone users to not only to view Microsoft Word and Excel documents, but they were able to create and edit them too. Today, there are business apps from Salesforce, SAP and Oracle along with business intelligence and HR apps. Companies can even lock down and locate a lost or stolen iPhone.
Business users are increasingly looking to take advantage of Apple iOS devices in the corporate environment, and as such IT organizations are looking for ways to allow access without compromising security, or risking loss of endpoint control. IT departments who have been slow to accept the iPhone are now looking for a remote access solution to balance the need for mobile access and productivity with the ability to keep corporate resources secure.
The F5 BIG-IP Edge Portal app for iOS devices streamlines secure mobile access to corporate web applications that reside behind BIG-IP Access Policy Manager, BIG-IP Edge Gateway and FirePass SSL VPN. Using the Edge Portal application, users can access internal web pages and web applications securely, while the new F5 BIG-IP Edge Client app offers complete network access connection to corporate resources from an iOS device; a complete VPN solution for both the iPhone and iPad.
The BIG-IP Edge Portal App allows users to access internal web applications securely and offers the following features:
- User name/password authentication
- Client certificate support
- Saving credentials and sessions
- SSO capability with BIG-IP APM for various corporate web applications
- Saving local bookmarks and favorites
- Accessing bookmarks with keywords
- Embedded web viewer
- Display of all file types supported by native Mobile Safari
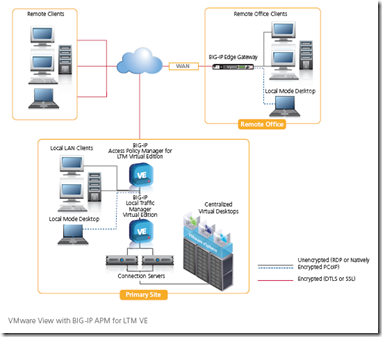
Assuming an iPhone is a trusted device and/or network access from an iPhone/iPad is allowed, then the BIG-IP Edge Client app offers all the BIG-IP Edge Portal features listed above, plus the ability to create an encrypted, optimized SSL VPN tunnel to the corporate network. BIG-IP Edge Client offers a complete network access connection to corporate resources from an iOS device. With full VPN access, iPhone/iPad users can run applications such as RDP, SSH, Citrix, VMware View, VoIP/SIP, and other enterprise applications. The BIG-IP Edge Client app offers additional features such as Smart Reconnect, which enhances mobility when there are network outages, when users roaming from one network to another (like going from a mobile to Wi-Fi connection), or when a device comes out of hibernate/standby mode. Split tunneling mode is also supported, allowing users to access the Internet and internal resources simultaneously.
BIG-IP Edge Client and Edge Portal work in tandem with BIG-IP Edge Gateway, BIG-IP APM and FirePass SSL VPN solutions to drive managed access to corporate resources and applications, and to centralize application access control for mobile users. Enabling access to corporate resources is key to user productivity, which is central to F5’s dynamic services model that delivers on-demand IT.
ps
Resources
| Connect with Peter: | Connect with F5: |
![o_linkedin[1] o_linkedin[1]](http://devcentral.f5.com/weblogs/images/devcentral_f5_com/weblogs/macvittie/1086440/o_linkedin.png) ![o_rss[1] o_rss[1]](http://devcentral.f5.com/weblogs/images/devcentral_f5_com/weblogs/macvittie/1086440/o_rss.png) ![o_facebook[1] o_facebook[1]](http://devcentral.f5.com/weblogs/images/devcentral_f5_com/weblogs/macvittie/1086440/o_facebook.png) ![o_twitter[1] o_twitter[1]](http://devcentral.f5.com/weblogs/images/devcentral_f5_com/weblogs/macvittie/1086440/o_twitter.png) | ![o_facebook[1] o_facebook[1]](http://devcentral.f5.com/weblogs/images/devcentral_f5_com/weblogs/macvittie/1086440/o_facebook.png) ![o_twitter[1] o_twitter[1]](http://devcentral.f5.com/weblogs/images/devcentral_f5_com/weblogs/macvittie/1086440/o_twitter.png) ![o_slideshare[1] o_slideshare[1]](http://devcentral.f5.com/weblogs/images/devcentral_f5_com/weblogs/macvittie/1086440/o_slideshare.png) ![o_youtube[1] o_youtube[1]](http://devcentral.f5.com/weblogs/images/devcentral_f5_com/weblogs/macvittie/1086440/o_youtube.png) |
Technorati Tags: F5, infrastructure 2.0, integration, cloud connect, Pete Silva, security, business, education, technology, application delivery, ipad, cloud, context-aware, infrastructure 2.0, iPhone, web, internet, security, hardware, audio, whitepaper, apple, iTunes