In this Lightboard, I light up some lessons on BIG-IP Access Policy Manager. BIG-IP APM provides granular access controls to discreet applications and networks supporting 2FA and federated identity management. You can also check out Chase's written article What is BIG-IP APM?
ps
Wednesday, July 26, 2017
Wednesday, July 19, 2017
Lightboard Lessons: Attack Mitigation with F5 Silverline
In this Lightboard Lesson, I describe how F5 Silverline Cloud-based Platform can help mitigate DDoS and other application attacks both on-prem and in the cloud with the Hybrid Signaling iApp. Learn how both on-premises and the cloud can work together to create a composite defense against attacks.
ps
ps
Labels:
ddos,
f5,
hybrid signaling,
iApps,
lbl,
security,
silverline,
waf
Tuesday, July 11, 2017
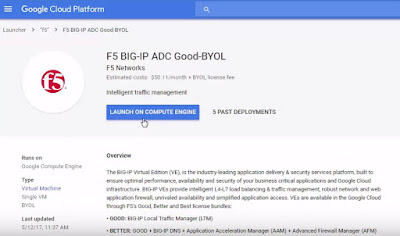
BIG-IP VE on Google Cloud Platform
Hot off Cloud Month, let’s look at how to deploy BIG-IP Virtual Edition on the Google CloudPlatform.
This is a simple single-NIC, single
IP deployment, which means that both management traffic and data traffic are
going through the same NIC and are accessible with the same IP address.
Before you can create this
deployment, you need a license from F5. You can also get a trial
license here. Also, we're using BIG-IP VE version 13.0.0 HF2 EHF3
for this example.
Alright, let’s get started.
Open the console, go to Cloud
Launcher and search for F5.
Pick the version you want.
Now click Launch on Compute
Engine.
I’m going to change the name so the
VM is easier to find… For everything else, I’ll leave the defaults.
And then down under firewall, if
these ports aren’t already open on your network, you can open 22, which you
need so you can use SSH to connect to the instance, and 8443, so you can use
the BIG-IP Configuration utility—the web tool that you use to manage the
BIG-IP.
Now click Deploy. It takes
just a few minutes to deploy.
And Deployed.
When you’re done, you can connect
straight from the Google console. This screen cap shows SSH but if you use the
browser window, you need to change the Linux username to admin in order to
connect.
Once done, you'll get that command
line.
If you choose the gcloud command
line option and then run in the gcloud shell, you need to put admin@ in front
of the instance name in order to connect.
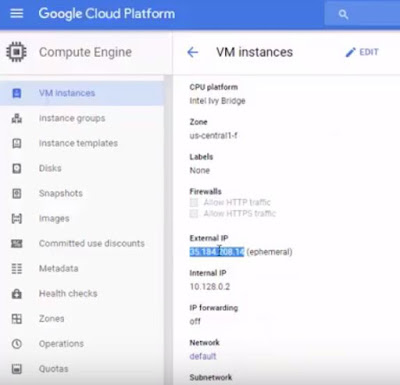
We like using putty so first we need
to go get the external IP address of the instance. So I look at the instance
and copy the external IP.
Then we go into Metadata > SSH
keys to confirm that the keys are there. (Added earlier), Whichever keys
you want to use to connect, you should put them here.
BIG-IP VE grabs these keys every
minute or so, so any of the non-expired keys in this list can access the
instance. If you remove keys from this list, they’ll be removed from BIG-IP and
will no longer have access. You do have the option to edit the VM instance and
block project-wide keys if you’d like.
Because my keys are already in this
list I can open Putty now, and then specify my keys in order to connect.
The reason that we're using ssh
to connect is that you need to set an admin password that’s used to connect to
the BIG-IP Config utility.
So I’m going to set the admin
password here… (and again, you can do these same steps, no matter how you
connect to the instance)
tmsh Command is: modify auth modify auth password adminAnd then: save sys config to save the change.
Now we can connect and log
in to the BIG-IP Config utility by using https, the external IP and port
8443. Now type admin and the password we just set.
Then we can proceed with
licensing and provisioning BIG-IP VE.
A few other notes:
- If you’re used to creating a self IP and VLAN, you
don’t need to do that. In this single NIC deployment, those things are
taken care of for you.
- If you want to start sending traffic, just set up your
pool and virtual server the way you normally would. Just make sure if your
app is using port 443, for example, that you add that firewall rule to
your network or your instance.
- And finally, you most likely want to make your external
IP address one that is static, and you can do that in the UI by choosing Networking,
then External IP addresses, then Type).
- If you need any help, here's the Google Cloud Platform/BIG-IP VE Setup Guide and/or
watch the full video.
ps
Labels:
application delivery,
big-ip,
cloud,
f5,
google cloud,
ve,
vm
Wednesday, July 5, 2017
DevCentral’s Featured Member for July – Vosko Networking’s Niels van Sluis
For almost two years Niels van
Sluis has worked as a Security Engineer for Vosko Networking. Vosko's security team focuses
on supporting security solutions from various vendors like F5, Check Point,
Cisco and RSA. Niels focuses is on F5 BIG-IP and Check Point. He started his
professional career about 20 years ago in the ISP industry as an Unix
Administrator, and switched to the public healthcare sector around 2001. In more
recent years, he’s moved more towards working on network security and design.
Apparently, having a Unix background helps a lot when working with modern
security devices, since most of them are running on some flavor of Unix. When
not working or spending time on DevCentral, he likes to travel, visit historic
places and enjoy nature. And Niels is DevCentral’s Featured Member for
July!
DevCentral: Tell us a little about the areas of BIG-IP expertise you have.
Thanks Niels! Check out all of Niels' DevCentral contributions, connect with him on LinkedIn and follow Vosko: @vosko.
DevCentral: Tell us a little about the areas of BIG-IP expertise you have.
Niles: My first encounter with BIG-IP was during my previous job. A colleague had been working with BIG-IP before and introduced it as a replacement for the KEMP load balancer that was currently in use. So, I had to attend the ‘Administering and Configure BIG-IP’ course. It was then – when I learned about iRules – I saw the full potential of this nifty device. But during my days there I didn’t do much with the BIG-IP as in terms to administration. I would only touch the box, if my colleague was on leave. This however changed when I started working for Vosko Networking. Within about a year’s time I’ve gone through the BIG-IP certification program, spend a lot of time on DevCentral and got my hands dirty in the field. The BIG-IP areas I’m most experienced in are LTM and APM. The most fun part for me are iRules (LX).DC: You are a Security System Engineer at Vosko Networking BV. Can you describe your typical workday?
NS: My typical workday depends whether I’m working on a project or not. When working on projects I often visit customers throughout the country to help them deploy new equipment or configure new services. Recently I’ve migrated quite a few Cisco ACE and Microsoft Forefront TMG deployments to the F5 BIG-IP platform. Other times I help customers upgrading their BIG-IPs or setting up more advanced APM configurations including SAML and SSO. When I’m not working on projects I work on support cases or trying out new stuff in our lab.DC: You have a number of F5 Certifications including most of the Technology Specialist (LTM, GTM, APM, ASM) certifications. Why are these important to you and how have they helped with your career?
NS: First of all, they are required for Vosko Networking to participate in the F5 Support Partner program. But more important to myself is that the F5 certification program helps to get deeper knowledge in to how the various BIG-IP modules work, how they relate (interact) to each other and what part the BIG-IP plays in modern network infrastructures. The certification program is also very practical; you can directly apply what you have been learning. It helped me to get more comfortable and confident in my day to day job.DC: Describe one of your biggest BIG-IP challenges and how did DevCentral helped in that situation.
NS: In my experience, there are BIG-IP challenges every day. I think this is the result of the BIG-IP being some kind of network-magic-box, that can do about everything. With most other security devices, one is limited to the functionality and settings the box is shipped with. But with BIG-IP, you can really be creative and think outside the box. If the required functionality is missing, you can build it yourself with iRules. And customers know this. I often go out to customers with a specific need, but when starting out it isn’t always clear if this is something the BIG-IP can do by default. In these situations, access to the DevCentral community is crucial. Even though BIG-IP isn’t an open source project, it’s amazing to see how members share their time, code and knowledge to help each other. For example, some code that really helped me out are Yann Desmarest’s APM Full Step Up Authentication and Stanislas Piron’s APM SharePoint authentication. Besides code, I think the Lightboard Lessons are awesome; very helpful!DC: Lastly, if you weren’t an IT admin – what would be your dream job? Or better, when you were a kid – what did you want to be when you grew up?
I think I wanted to be an electrician when I was young, but I’m pretty sure that isn’t my dream job. As long as I’m able to learn new things and have new challenges, I’m happy how things are. I think I’m useless for any other job that doesn’t require a keyboard. Thanks for the privilege for being a featured member and thanks for the Lightboard Lessons as well. I really enjoy them.
Thanks Niels! Check out all of Niels' DevCentral contributions, connect with him on LinkedIn and follow Vosko: @vosko.
Subscribe to:
Comments (Atom)