Not the device's but your behavior. Harvard Business School researchers wanted to determine if the type of device people use changes how they act around other people. Does device size affect assertiveness? Does interacting with a device of a certain size, affect how you behave afterword? Or, Is Your iPhone turning you into a Wimp?
If you just can't stand the suspense, in a word, Yes.
Many of us are aware that body language can communicate so much more than words. If you watch (and can understand) people's body language, you can learn much more than just what they are saying. Are they uncomfortable or are they hiding something. Are they imagining something or recalling from memory. You might have even heard of micro-expressions - those little head scrunches, slight eye squint or a tight jaw that sends a message. In addition, by adopting certain postures, body chemistry and behavior can be affected. For example, standing over someone's desk with arms wide, generally brings more assertiveness than sitting across with arms and legs crossed. So how about our posture while using a mobile device since we spend an average of 58 minutes per day our smartphones? Would it then make sense that a larger (arms wide) screen person would be more assertive than someone using a smaller (arms crossed) screen?
Apparently so.
 The study, 'iPosture: The Size of Electronic Consumer Devices Affects Our Behavior,' looked at how the body posture inherent in operating everyday gadgets affects not only your body, but also your demeanor. It showed that working on a relatively large machine (like a desktop computer) causes users to act more assertively than working on a small one (like an iPod).
The study, 'iPosture: The Size of Electronic Consumer Devices Affects Our Behavior,' looked at how the body posture inherent in operating everyday gadgets affects not only your body, but also your demeanor. It showed that working on a relatively large machine (like a desktop computer) causes users to act more assertively than working on a small one (like an iPod).
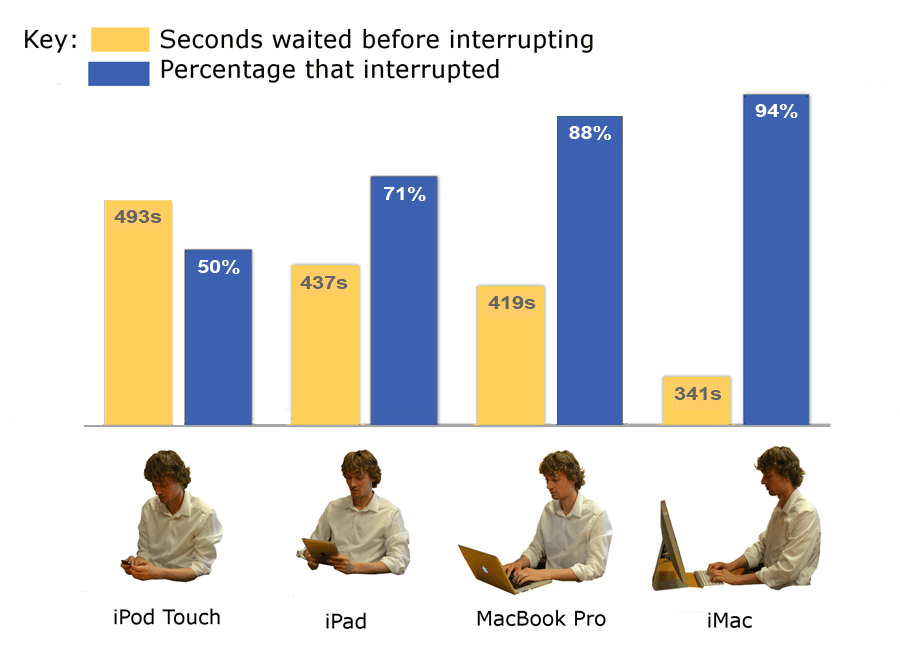
The researchers asked participants to perform randomly assigned tasks on one of four different sized devices: iPod Touch, iPad, MacBook Pro Laptop or iMac Desktop. They answered a survey, played a gambling game and a few other tasks and when they were done, the researcher told them, 'I will get some forms ready for you to sign so I can pay you and you can leave. If I am not here in five minutes, please come get me at the front desk.' Instead of retuning on time, the researches waited at least 10 minutes and noted if/when a participant came to the front desk.
The participant's device size greatly affected who made the move to the front. Of the participants using a desktop computer, 94% took the initiative to fetch the researcher but those using the iPod Touch, only 50% left the room. And among those who did leave the room, the device size seemed to affect the amount of time they waited to take action. The bigger the device, the shorter the wait time. On average, desktop users waited 341 seconds before fetching the experimenter, while iPod Touch users waited an average of 493 seconds.
According to the researchers, the results indicate that expansive body postures lead to power-related behaviors, even in cases where the posture is incidentally induced by the size of the gadget or computer.
So what does all this 'human behavior' stuff mean for BYOD? Not really sure but fun to think about it. Will those seeking advancement in the workplace, gravitate toward tablets? Does offering a larger device to a normally shy worker bring out their assertiveness? Do you have the annoying know-it-all use the smallest screen possible? Might be interesting to look around the office and what devices employees use to see if the study results match your work environment.
ps
Related:
- Device size affects your assertiveness, study says
- Is Your iPhone Turning You Into a Wimp
- iPosture: The Size of Electronic Consumer Devices Affects Our Behavior
- Power Posing: Brief Nonverbal Displays Affect Neuroendocrine Levels and Risk Tolerance
- Americans spend 58 minutes a day on their smartphones
- The Prosecution Calls Your Smartphone to the Stand
- Q. The Safest Mobile Device? A. Depends
- 50/50 Odds for BYOD
- BYOD–The Hottest Trend or Just the Hottest Term
- Will BYOL Cripple BYOD?
- BYOD 2.0 – Moving Beyond MDM with F5 Mobile App Manager
- Is BYO Already D?
| Connect with Peter: | Connect with F5: |
| |
